The NIST RMF process is the basis of our overall approach for cybersecurity and application development. Our engineers and analysts are familiar with the RMF and can perform work at any step, including evaluating system characteristics, system designs, operational processes, controls, and operational trends. OSI has successfully delivered end-to-end Federal Information Security Management Act (FISMA) compliance and assurance services.
Cyber Security
OSI’s System Engineering methodology links directly to the Risk Management Framework. Following are our System Engineering key phases:
· Need, Feasibility, Concept, and Analysis
· Architecture, Design & Development
· Test and Integrate
· Validate
· Prepare, present, and record authorization
· Sustainment
Need, Feasibility, Concept, and Analysis activities for IA are conducted for RMF Step 1. Step 2 occurs in Architecture, Design & Development; Step 3 occurs in Test and Integrate; Step 4 takes place in Validate. Although RMF Step 5 is an inherently government function, our activities to prepare, present, and record authorization are generally covered by the Validate activities in our Methodology. Step 6 maps to our Sustainment activities.
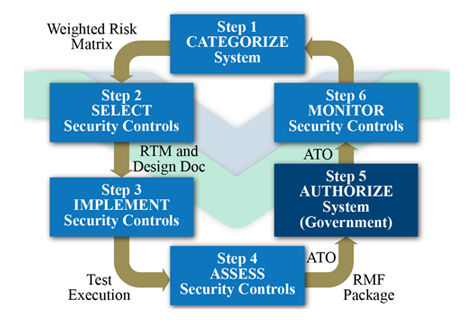
The graphic above shows the RMF for cybersecurity. In Step 1 we use DoD 8510.01 and NIST 800-59 (Guideline for Identifying an Information System as a National Security System) and NIST 800-60 (Guide for Mapping Types of Information and Information Systems to Security Categories) to categorize and assess the risks associated with the top-level systems design requirements. This includes the
identification of system components that will use mobile or cloud technology, client/server, or distributed (web) processing designs. Step 1 contributes to the functional requirements and identification of risks.
Step 2 determines the overall design of the cybersecurity configuration, the network that will act as the host in the Design Document, and the discrete set of cybersecurity controls in the Requirements Traceability Matrix (RTM). Site surveys are used to determine the approach to physical security and installation requirements. Selection includes public key infrastructure (PKI) controls such as user identity management (common access card [CAC] integration), server and data object certificates.
Typical controls implemented in Step 3 include firewalls/guards (Cisco and Juniper), IDSs (HP Tipping Point), and information sensors of computer and network systems that are used to mitigate security risks.
Step 4 is the final measurement of control performance. Code-level, compliance, and tactical testing prepare the final A&A package for Step 5. We do prepare, present, and record all artifacts involved in the authorization process. On authorization, in Step 5, the controls move into sustainment where control measures are monitored, exceptions noted, and potential incidents alerted.